Contents
Introduction
Cybersecurity is paramount in this modern technological world, small businesses are increasingly targeted by cyber threats. It is imperative for small businesses to implement cybersecurity Strategies practices to safeguard their digital operations. From network security and multifactor authentication to cybersecurity insurance and incident response plans, we’ll cover practical steps tailored to small businesses. By adopting these practices, you can enhance your cybersecurity Strategies, safeguard critical data, and ensure your business thrives securely in today’s interconnected world. Join us on this journey to fortify your cyberspace and protect your small business from potential threats.
Network Security
Network security encompasses a wide array of strategies employed to safeguard digital infrastructure in order to ensure Cybersecurity . It pertains to access control, encompassing authorization for establishing and enforcing permissions and authentication for verifying the identities of users and devices. Intrusion Detection and Prevention Systems (IDS/IPS) identify any suspicious activities and take appropriate measures in response. Network segmentation isolates segments to prevent intruders from moving laterally. Patch management ensures the perpetual up-to-date of software and hardware with security updates. To maintain proactive defence, it is imperative to leverage Threat Intelligence. Specialized protection is provided by security appliances such as content filters and intrusion detection systems.
Firewalls and Virtual Private Networks
Firewalls serve as a barrier between internal networks and the untrusted outside world, controlling incoming and outgoing traffic based on predefined cybersecurity Strategies. They help prevent unauthorized access, filter out malicious traffic, and deter potential threats. On the other hand, VPNs establish secure, encrypted connections over public networks, such as the internet. By securely conveying data, they ensure data confidentiality and integrity, making it extremely challenging for unauthorized parties to intercept sensitive information. Combining firewalls and VPNs offers a layered defence strategy, This multi-faceted approach significantly enhances overall network security, making it a vital part of modern cybersecurity strategies small businesses to implement.
Multifactor Authentication
In order to strengthen security, Multifactor authentication, which requires users to submit multiple forms of identity during login, is an essential security practice. Even in the event that an illicit attacker manages to breach one authentication factor—like a password—this strong defense keeps access from becoming unlawful. When logging in using Multifactor authentication, users must provide several authentication factors, such as passwords, fingerprints, or security tokens which lower the risk of data breaches and illegal system access. Access is allowed if these match the data that has been stored.
It is one of crucial Cybersecurity Strategies small businesses need to implement with limited funding. Cybercriminals frequently target SMBs because they believe they have vulnerabilities.
Cybersecurity Insurance
Cybersecurity insurance, is one of crucial cybersecurity Strategies small businesses can use to mitigate financial risks arising from cyber threats and data breaches. It functions as a financial safety net, providing coverage for various costs, including data recovery, legal compliance, public relations, and potential liabilities incurred in the aftermath of a security incident. Furthermore, it incentivizes companies to invest in resilient measures in cybersecurity strategies by offering reduced premiums to those with strong cybersecurity Strategies. While not a substitute for comprehensive security protocols, cybersecurity insurance is an integral element of a holistic cybersecurity approach, enabling organizations to manage the financial repercussions.
Each weekday this #CybersecurityAwarenessMonth, we’ll share quick tips for in-house lawyers to apply legal first aid during a security incident. Today, Kandi Parsons presents Tip #6: Cyber Insurance. Check back each day for more! #Cybersecurity #ZGCyber https://t.co/st5HwxIII1 pic.twitter.com/o4NlHaVv8T
— ZwillGen (@ZwillGen) October 9, 2023
Workforce Training
A crucial security step for Small and Medium Enterprises looking to strengthen their cybersecurity Strategies is employee training. In the current digital environment, which is marked by cyberthreats, workforce awareness and training are essential cybersecurity strategies small businesses can implement. Thorough training programs are essential; they should demonstrate to staff members how to spot social engineering techniques, promote safe password usage, and recognize phishing attempts. It is imperative to emphasize the importance of routine software updates and responsible online conduct.
Workers need to be prepared to report security incidents quickly and handle them professionally, which will cut down on response times and possible harm.
Here is a video for clear understanding of How important training employees and Zero trust networks is ?
Email and Website security
Email communication necessitates having safeguards in place to secure sensitive data and prevent phishing attempts, such as spam filters, antivirus software, and encryption. In the digital age, data security and preserving the integrity of communication channels depend on upgrading email security protocols.
For companies, having a secure website is essential. Using web application firewalls, applying access controls, upgrading software and plugins often, and enforcing HTTPS encryption are examples of common approaches. Sustaining consumer confidence, avoiding data breaches, and protecting businesses’ online identify all depend upon having an effective website security system.
Email and Website security are 2 vital cybersecurity strategies small businesses can enhance.
Encryption and Recovery
To ensure data confidentiality and integrity, encryption transforms data into a coded format that can only be decoded using the right decryption key. It is employed to guard data both during transmission and while it is at rest, preventing unwanted access.
In contrast, data recovery refers to the procedure of retrieving lost or corrupted data, frequently using redundancies or backups. Effective data recovery techniques are essential to reduce downtime and data loss in the case of data breaches, system malfunctions, or natural disruptions.
In order to ensure data protection and business continuity in the face of cybersecurity threats and unforeseen disruptions, data recovery and encryption are both crucial cybersecurity strategies small businesses should implement.
Infrastructure Security
This approach is applicable to a variety of systems, including contemporary cloud and edge environments as well as conventional data centers. Enterprise infrastructure security frameworks typically consist of four layers: physical, network, application, and data security. These layers work together to protect against a variety of threats, including cyberattacks, data breaches, and physical weaknesses. The use of endpoint security solutions, such as sandboxing, antivirus software, and URL filtering, is essential for improving defence against online threats. In the connected digital world of today cybersecurity strategies small businesses should also includes physical infrastructure, an all-encompassing strategy is essential for maintaining the dependability and resilience.
Incident Response Plan
Incident response plan is an organized method to ensure security and to properly handle crisis. It acts as a thorough manual, outlining what has to be done in the event of a security and breaches.
Important elements including incident identification, containment, eradication, and recovery protocols are usually included. In order to limit downtime, it also specifies responsibilities and communication channels, ensuring a coordinated and quick response. In today’s security climate, where cyberattacks are more of a “when” than a “if,” incident response plans are crucial. Organizations can effectively handle crises, safeguard confidential information and lessen the financial and reputational damage.
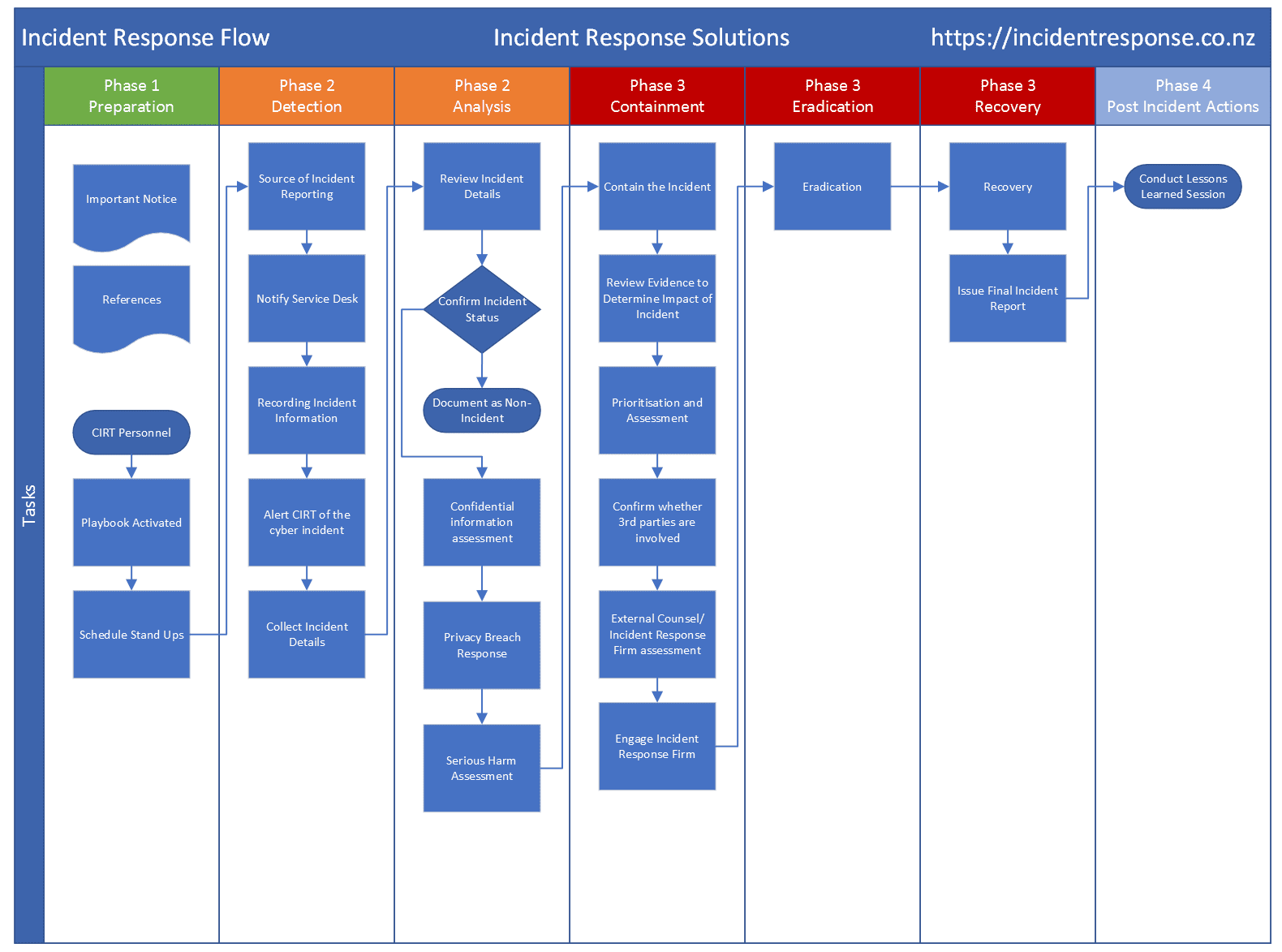
Credits: Incident Response Solutions
Internal Security Policies
Cybersecurity policies in a company cover a variety of important topics with the goal of protecting confidential information and guaranteeing adherence to legal obligations. A crucial element is legal compliance, which requires firms to abide by all applicable laws and rules on privacy and data protection.
A major part of this architecture is vendor security. To make sure that these organizations do not endanger their data or operations, by following cybersecurity strategies small businesses must evaluate and keep an eye on the their third-party contractors.
Organizations must conduct regular audits in order to evaluate the efficacy of their security measures and spot any potential weaknesses. To maintain a strong security posture, these evaluations frequently involve cybersecurity audits and penetration testing.
Conclusion
Cybersecurity is paramount for small businesses. This comprehensive strategy equips them to counteract the cyber attacks ensuring the security of their operations, data, and reputation. Prioritizing cybersecurity Strategies is essential for safeguarding sensitive data and maintaining business continuity in an increasingly interconnected world.
Sparity will be your collaborative partner to protect your business from cyber attacks.