Contents
Introduction
In our fast-paced digital environment, the realm of cybersecurity is filled with common misconceptions that can leave businesses exposed to a range of risks. These cybersecurity myths often lead to the mistaken belief that external hackers are the sole threat, that cybersecurity is only about thwarting hacking attempts, that increased financial investments equate to enhanced protection, or that advanced technology alone can ensure safety against continually changing cyber threats. In this comprehensive exploration, we will dispel these prevalent cybersecurity myths, shed light on the complex nature of digital vulnerabilities, and emphasize the importance of a holistic cybersecurity approach.
By dispelling these misconceptions, organizations can enhance their defences in the constantly evolving field of cybersecurity. Join us as we unite to address these cybersecurity myths and strengthen our digital security together.
Threats are only from External Hackers – Addressing Insider threats
One of the main yet common Cybersecurity myths is the notion that external hackers alone pose threats to a company’s security. This myth oversimplifies the intricate nature of cybersecurity risks, presuming that the primary danger originates exclusively from outside an organization’s digital boundaries. In reality, the cybersecurity landscape is multifaceted.
While external hackers are a genuine concern, they constitute just one aspect of a complex web of potential vulnerabilities. Internal actors, encompassing both malicious and inadvertently negligent employees, pose a significant risk. Additionally, third-party vendors, supply chain vulnerabilities, insider threats, physical breaches, and social engineering attacks all contribute to this intricate tapestry of risks. Understanding this diversity is essential for a comprehensive cybersecurity strategy.
Stuxnet, a sophisticated malware, targeted Iran’s nuclear program by exploiting internal vulnerabilities via infected USB drives. This real-world examples dispels the cybersecurity myths that external hackers are the sole cybersecurity threat.
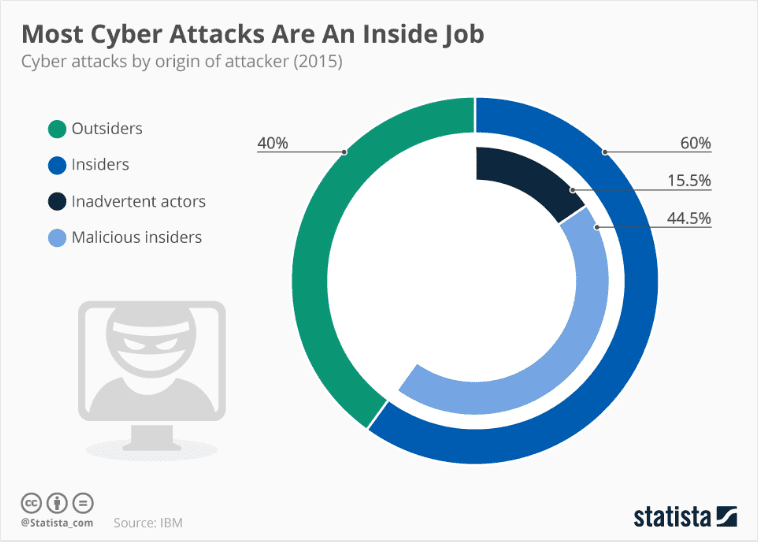
A report from Statista showing how important it is to focus on Insider threats as well.
Spectrum of Cybersecurity – More than just Hacking
While hacking is a notable cybersecurity concern, it’s essential to dispel the cybersecurity myths revolves solely around thwarting hackers. Cybersecurity ensures data protection and system integrity, while hacking involves unauthorized actions to gain personal information or disrupt and manipulate data. Cybersecurity encompasses a much broader spectrum of technical aspects, ranging from safeguarding sensitive data and ensuring compliance with data protection regulations to fortifying network and endpoint security, and implementing robust incident response plans.
It also includes managing user access, securing cloud environments, promoting secure development practices, fostering employee awareness, addressing physical security concerns and managing user access effectively through Identity and Access Management (IAM). IAM plays a pivotal role in ensuring only authorized individuals can access sensitive resources, emphasizing the importance of this multifaceted approach to address cybersecurity myths.
Watch this video of Bob Kalka from IBM Security addressing issues in a detailed manner for clear understanding.
Is More Money Always More Protection?
The myth that increased spending on cybersecurity guarantees enhanced safety is fundamentally flawed. In reality, a linear correlation between expenditure and security simply does not exist in the complex landscape of cyber threats. Like in economics, the law of diminishing returns applies. Increasing investments initially brings significant defence improvements but becomes less cost-effective over time.
Efficient cybersecurity demands a nuanced approach. Rather than indiscriminate financial pouring, organizations should invest judiciously. Focus on risk assessment, targeted security training, advanced threat detection systems, regular updates, and collaborative threat intelligence sharing. These elements, grounded in technical strategy, amplify security without the burden of exponential spending. Dispelled cybersecurity myths such as “more money, more safety”, replaced by a smarter, more efficient paradigm where strategic investments, not sheer quantity, determine cyber resilience.
The Equifax breach (2017) demonstrated that even massive cybersecurity budgets can’t prevent attacks without effective risk management.
Believing that a company won’t face financial losses if its data is accessed, solely because attackers aren’t targeting transactions, requires reconsideration.
IBM Security released its annual Data Breach Cost Report, revealing record-high costs and prompting diverse responses from businesses.
Today @IBMSecurity released the annual Cost of a Data Breach Report, showing all-time high data breach costs–leaving businesses divided in how they plan to handle the increases. See the findings: https://t.co/CLq01D3U0X pic.twitter.com/eSYmBhCx99
— IBM News (@IBMNews) July 24, 2023
Guaranteed Cybersecurity through Advanced Technology
The misconception that increased technological advancement inherently equates to heightened cybersecurity is widespread. However, the reality of cybersecurity extends far beyond the sophistication of tools and systems. As technology progresses, the attack surface often expands, introducing more potential vulnerabilities. IoT devices, interconnected systems, and cloud infrastructure can inadvertently provide entry points for cybercriminals. The constant emergence of zero-day vulnerabilities, previously unknown to security systems, poses a persistent threat.
The human factor remains a significant vulnerability. Social engineering, phishing attacks, and insider threats continue to exploit human weaknesses. Resource allocation and the risk of a false sense of security are also critical considerations. Advanced technology is undoubtedly crucial in combating cyber threats. However, it must be accompanied by a comprehensive cybersecurity strategy that includes proactive measures, employee training, regular assessments, and an incident response plan. Addressing these cybersecurity myths is paramount.
Transforming Misconceptions into Reality
Misconceptions about cybersecurity often lead businesses to rely solely on firewalls, secure cloud infrastructures, and robust multi-factor authentication (MFA) mechanisms. However, these beliefs can lead to vulnerabilities if not critically examined.
The belief that anonymity protects a company from cyberattacks is misleading assumption under cybersecurity myths.. Cybercriminals exploit known vulnerabilities indiscriminately. Automated scanning tools scour the internet for weaknesses, making every business a potential target.
Believing that cyber attackers solely focus on prominent organizations like banks is an outdated assumption. In reality, malicious actors target vulnerabilities across various industries, be it in a business-to-business (B2B) context or otherwise. Their objectives encompass financial gain, data theft, or causing operational disruptions. This emphasizes the importance of a comprehensive cybersecurity stance.
The “misconception” of the “time to detection” is dangerous, as breaches can remain undetected for extended periods, affording attackers ample opportunity to exfiltrate data or implant malware. Constant vigilance, threat monitoring, and proactive security measures are essential for businesses, irrespective of their industry or market focus. Dispelling these Cybersecurity myths is crucial for safeguarding digital assets effectively.
Conclusion
Debunking prevalent cybersecurity myths is vital for businesses navigating the digital sphere. Understanding the multifaceted nature of threats, avoiding the assumption that increased spending guarantees safety, and recognizing that technology alone cannot ensure security are essential steps. These shifts in perspective empower organizations to adopt comprehensive and adaptive cybersecurity strategies, ultimately safeguarding their digital assets in a dynamic and continually evolving context of risks.
Sparity provides all cybersecurity services, making it a valuable partner for your business.