The term “DSPM” gained formal recognition when Gartner highlighted DSPM as a new security category in 2022, describing it as a way to bring visibility and control to sprawling enterprise data estates. Later, analyst firm GigaOm expanded on the concept by defining DSPM in operational terms “Focusing on automated discovery, classification, policy enforcement, and continuous risk assessment across structured and unstructured data environments.”
Now DSPM is considered as a modern evolution beyond traditional tools like DLP or CSPM purpose-built for cloud-first, AI-driven enterprises.
Why DSPM Is Important
With massive data being generated and stored in large volumes across dozens of platforms it creates three major risks-
- Unknown sensitive data – Teams are unaware of regulated data.
- Over-permissioned access – Confidential data being visible to multiple users/ systems.
- Compliance exposure – Proof of control is required to regulations like GDPR, DPDP, and HIPAA.
DSPM plays a major role by giving security and compliance leaders:
- A live inventory of sensitive data.
- Visibility into risky access paths.
- Alerts when policies are violated.
- Evidence for audits and regulators.
Table of Contents
How data security posture management works
DSPM workflow follows a structured, data-centric approach to identifying, managing, and mitigating security threats:
- Discover- Automatically detect sensitive data across cloud, hybrid, and on-premises environments.
- Classify- Data is characterized based on sensitivity, type, and compliance requirements.
- Assess- Close evaluation of Data exposure, access permissions, and associated risks is done.
- Detect- Continuously track data activity, access patterns, and policy violations.
- Remediate- Required action is taken to reduce risks like adjusting access, applying encryption, or alerting security teams.
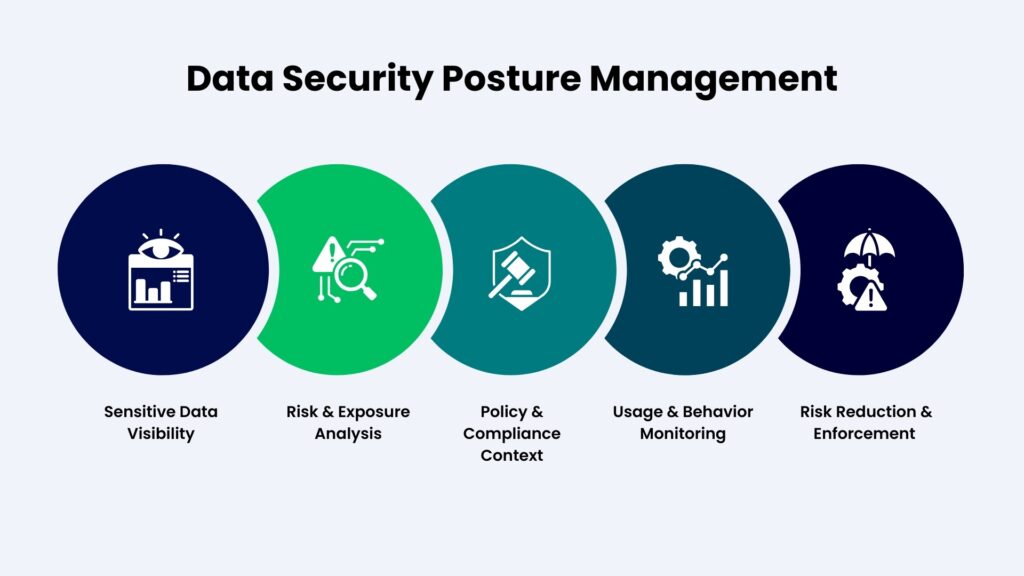
The Key capabilities of DSPM
Discovery and classification
DSPM goes beyond finding obvious databases or storage buckets. It focuses on exposing the real risk layer around data, how sensitive information is spread, copied, accessed, and used across modern cloud and AI ecosystems.
It covers-
- Shadow data repositories
- Sensitive data inside unstructured sources
- AI-ready and training datasets
- Cross-border data locations
- Over-exposed datasets
- Dormant but risky data
Data & AI Governance Intelligence
DSPM builds a unified, real-time view of how data and AI systems interact across the enterprise. It starts by correlating metadata from cloud platforms, SaaS tools, analytics engines, and machine-learning pipelines. Post this, it reveals which datasets feed AI models, the accessibility, and whether configurations create security or compliance risk.
As generative AI adoption accelerates, DSPM acts as a central governance layer to help organizations control data exposure, enforce policy, and validate responsible AI use.
It focuses on-
- Data feeding analytics, ML, and GenAI workloads
- AI models, agents, and shadow AI services
- Security posture and encryption controls
Security Posture Management & Risk Correlation
DSPM continuously evaluates how security settings impact sensitive and regulated data across cloud platforms, SaaS tools, and enterprise data systems. After scanning for misconfigurations such as public storage, weak encryption, excessive permissions, or missing logging, DSPM identifies exposure points that could lead to security or compliance incidents.
Its ability to correlate posture findings with data context is commendable as it doesn’t focus on each misconfiguration as a standalone issue. By using graph-based analysis and policy-driven risk models, it surfaces high-impact risk scenarios created by the interaction of multiple weak signals commonly known as “toxic risk combinations.”
DSPM detects and prioritizes scenarios such as:
- Regulated datasets exposed through publicly reachable storage services
- AI training pipelines consuming sensitive data without consent or governance controls
- Cross-region replication of restricted data outside approved jurisdictions
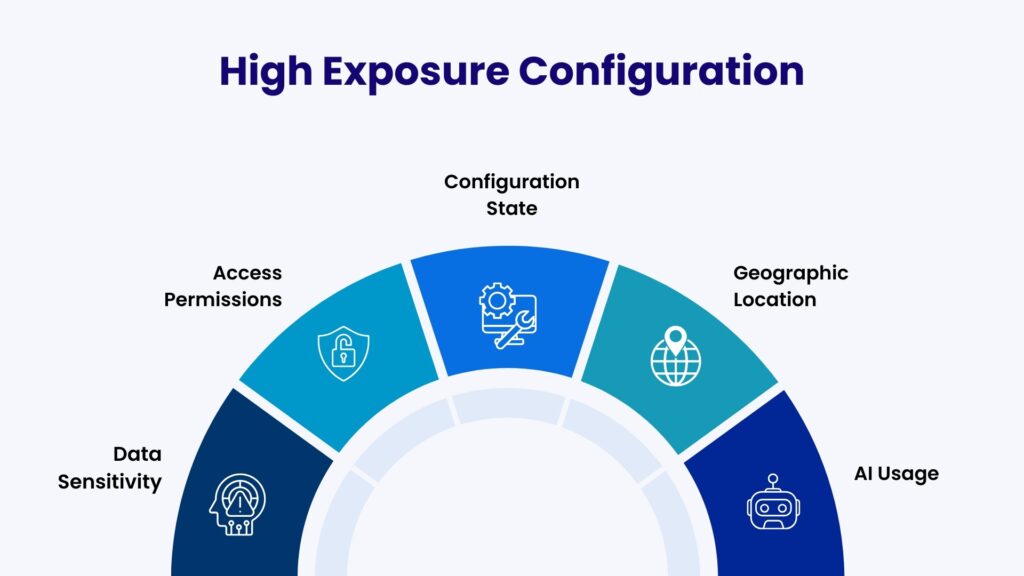
Data Access Intelligence and Control
Often regarded as the Enforcement Layer, access intelligence governs exposure. It has control over who should be allowed to access the data and how to enforce that safely.
It focuses on-
- Mapping actual access paths (users, roles, service accounts, AI agents)
- Detecting over-privileged access to sensitive datasets
- Understanding how access is used, not just granted
- Enforcing least-privilege policies at a granular level
Most data breaches occur when the data access is excessive, misused or poorly enforced. Regulators expect organizations to demonstrate active access governance, not just being limited to passive monitoring. DSPM addresses this by enabling policy-driven access controls ensuring sensitive data stays protected while remaining usable for legitimate business needs.
Data Flow Intelligence & Governance
Here DSPM focuses on understanding how sensitive data moves, changes, and is reused across systems over time. It continuously maps data lineage to show where data originates, how it is transformed, which systems and applications consume it, and whether it crosses regulatory or organizational boundaries. By tracking these flows, DSPM enables organizations to enforce governance policies, detect unauthorized transfers, prevent data leakage, and ensure compliance with data residency and privacy requirements throughout the data lifecycle.
It helps by-
- Eliminating blind spots and supporting in audit and compliance reporting.
- Preventing unauthorized use and ensures data is handled correctly.
- Reduces the chance of data leaks and compliance violations.
ROT Data Minimization – (Redundant- Obsolete- Trivial Data)
Businesses overlook the fact that old copies, unused files, and low-value datasets silently increase risk. DSPM plays a critical role by continuously scanning environments to identify sensitive data that no longer is needed but still falls under regulatory scope.
DSPM builds a live data inventory using metadata analysis, activity signals, and retention policies. It identifies duplicates, inactive datasets, and data past retention thresholds, then flags them for deletion, archiving, or tighter controls. In this way, less unnecessary data helps in lower compliance exposure and reduced risk of sensitive data being misused.
It assists in-
- Detects near-duplicate data created through analytics pipelines and backups
- Prioritizes ROT data remediation based on sensitivity and regulatory impact
- Supports defensible deletion workflows with audit trails
AI Security & Governance
As organizations deploy machine learning and generative AI, DSPM helps identify which datasets are used for training, inference, or retrieval. This is crucial to determine whether those datasets contain regulated or sensitive information.
This step allows teams to detect risks such as sensitive data feeding models without consent, improper access by AI agents, or exposure through prompts and outputs.
It helps to-
- Flags AI workloads using outdated or improperly labeled data
- Supports governance over retrieval-augmented generation (RAG) data sources
- Enables separation of training, inference, and evaluation datasets
Compliance Automation
Here compliance automation implies to turning data security controls into continuous, automated processes rather than just manual checklists. DSPM constantly evaluates data against regulatory requirements. The discovered data and security controls are mapped to frameworks like GDPR, DPDP, HIPAA etc. Evidence collection is automated and policy adherence is monitored to generate audit-ready reports. This helps to reduce compliance overhead, improves accurate results and assists the organization to follow compliance.
It supports in –
- Maintains real-time compliance posture across multiple jurisdictions
- Tracks policy violations triggered by configuration or access changes
- Supports human-in-the-loop approvals for sensitive compliance actions
Why Enterprises Must Operationalize DSPM
Effective DSPM requires deep visibility into where sensitive data lives, how it flows across systems, who can access it, and how security and compliance controls are enforced in real time. It brings together data governance, cloud security, access management, and compliance into a unified operational approach.
Organizations that treat DSPM as a foundational capability, rather than a reactive control, are better positioned to reduce risk, meet regulatory obligations, and scale digital innovation with confidence. This is where a strong security and cloud foundation matters. By helping enterprises strengthen their cloud security posture, governance frameworks, and data protection practices, Sparity enables organizations to take a practical, scalable approach to DSPM one that protects data wherever it resides and supports long-term resilience.
Applying DSPM in Real Enterprise Environments
We have worked with organizations to secure data across cloud, hybrid, and enterprise IT environments addressing foundational DSPM objectives such as data visibility, access control, risk reduction, and regulatory compliance. By strengthening cloud security posture and governance frameworks, Sparity helps organizations build the operational maturity required to manage sensitive data effectively at scale.
Start building a data security posture that scales with your cloud and AI ambitions.
Talk to Sparity.